Certifications: ISO 27001 | ISO 9001 | Cyber Essentials (UK)
delivering CybersecurityExcellence
Protecting businesses and thousands
of their customers daily
Our Services
Consulting Services
- Governance, Risk and Compliance
- Cybersecurity Advisory
- Data Security
- Post-Quantum/ PQC Cyber Readiness
- Cybersecurity Maturity Assessment
- Cybersecurity Solution Design and Implementation
Professional Services
- Accelerate the Solution implementation
- Adoption of unique expertise and best practices.
- Scale professional services capability and geographic coverage for cybersecurity product Vendors
Managed Services
- Security Operations Center
- Assurance Services
- GRC Services
- Staff Augmentation/RE
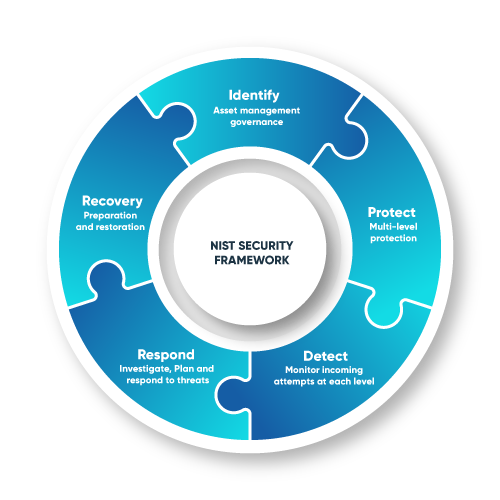
NIST Cybersecurity Framework
Sinevis strives to provide it’s clients services based on the most robust Cybersecurity framework -NIST. Our services and expertise are aligned with it’s methodologies at the same time we are vigilant enough to bend the rules to strengthen it further.
Projects delivered across
Countries
35
+
Unique customers
500
+
Service Industries
12
+
What Is The Criteria For Selecting A Reliable Cybersecurity Services Provider?
Listen to their questions – Reflect & Map to your requirements. It is critical that your services provider is open to adjust as per your organisation needs.
Our Expertise
Sinevis services are aligned to build a secure and trusted environment for your business
Post-Quantum Cybersecurity
Prepare for tomorrow’s quantum threats — with a roadmap, tools and guidance to get quantum cyber-ready now.
Learn More
Security Risk & Compliance Management
Sinevis Provides robust risk and compliance management services, which allow you to identify, govern and manage security risks. Our due diligence services allow us to remain compliant with evolving legal and regulatory requirements.
Learn More
Security Monitoring & Response (SECOPS)
Empower your Security Operations (SecOps) with unified monitoring, threat detection and responsive incident workflows, anchored by a powerful SIEM platform
Learn More
Security Testing & Assurance
Validate and harden your environment with proactive security-testing and assurance services – we uncover vulnerabilities, evaluate controls and verify remediation so your systems stay resilient.
Learn More
Application Security
Protect your applications end-to-end with cloud-delivered WAF, bot mitigation (ABP), and full application-layer DDoS defense.
Learn More
Data Security
Fortify your data at every layer with full-spectrum database security — activity monitoring (DAM), DB encryption, file activity monitoring (FAM)
Learn More
Identity & Access Management
Unlock business agility with identity-first security: provisioning, governing and removing access at speed.
Learn More
Cyber Physical Systems (OT/IoT)
Whether it’s IoT sensors or OT controllers, we deliver continuous protection so your systems stay resilient and reliable.
Learn More
Our Blog
In our blog, you will find some useful contents to help you understand how and what it takes to implement a strong cybersecurity culture.